444 Alaska Avenue
Suite #BAA205 Torrance, CA 90503 USA
+1 424 999 9627
24/7 Customer Support
sales@markwideresearch.com
Email us at
Suite #BAA205 Torrance, CA 90503 USA
24/7 Customer Support
Email us at
Corporate User License
Unlimited User Access, Post-Sale Support, Free Updates, Reports in English & Major Languages, and more
$3450
Market Overview
In the ever-evolving landscape of cybersecurity, User Activity Monitoring (UAM) solutions have emerged as a crucial defense against potential threats. These solutions play a pivotal role in tracking, recording, and analyzing user behavior within an organization’s network, applications, and systems. By offering insights into user actions, UAM solutions empower businesses to enhance their security posture and ensure compliance with regulatory standards.
Meaning
User Activity Monitoring (UAM) solutions refer to the suite of technologies and practices designed to monitor and analyze the actions and behaviors of users within an organization’s digital ecosystem. This encompasses tracking user logins, application usage, file access, data transfers, and other activities that occur within the IT infrastructure. The aim is to identify anomalies, potential security breaches, and policy violations, ultimately safeguarding sensitive information and maintaining the integrity of digital operations.
Executive Summary
In an era where data breaches and cyberattacks continue to pose significant threats to businesses across industries, User Activity Monitoring (UAM) solutions have emerged as a critical component of proactive cybersecurity strategies. These solutions offer real-time visibility into user actions, allowing organizations to detect and respond to potential threats swiftly. As the digital landscape expands, the UAM market is witnessing substantial growth, driven by the increasing recognition of the importance of insider threat detection and compliance management.

Important Note: The companies listed in the image above are for reference only. The final study will cover 18–20 key players in this market, and the list can be adjusted based on our client’s requirements.
Key Market Insights
The User Activity Monitoring (UAM) solutions market is propelled by several key insights. Firstly, the rising frequency of insider threats and data breaches has escalated the demand for robust UAM solutions. Organizations are recognizing that a significant portion of security incidents originate from within their own ranks. UAM solutions provide the means to identify unusual or unauthorized activities that may indicate insider malicious intent.
Market Drivers
Several factors drive the adoption of User Activity Monitoring (UAM) solutions. The proliferation of remote work, bring-your-own-device (BYOD) policies, and cloud-based applications has expanded the attack surface for cyber threats. This has catalyzed the need for UAM solutions to maintain visibility and control over user activities across diverse environments. Additionally, stringent regulatory requirements mandating the monitoring of user actions to ensure data privacy and security are compelling organizations to invest in UAM solutions.
Market Restraints
Despite the growing demand for UAM solutions, certain market restraints need consideration. Privacy concerns related to employee monitoring and data collection can pose challenges, especially in regions with stringent data protection regulations. Striking a balance between security and privacy is essential. Moreover, the complexity of implementing UAM solutions across large and intricate IT infrastructures can be a barrier, requiring substantial resources and expertise.
Market Opportunities
Amid the challenges, opportunities abound in the UAM solutions market. The integration of artificial intelligence and machine learning technologies promises to enhance the accuracy of anomaly detection and reduce false positives. As the market matures, there’s potential for solutions that offer seamless scalability, simplified deployment, and intuitive user interfaces, catering to businesses of all sizes.
Market Dynamics
The User Activity Monitoring (UAM) solutions market operates within dynamic dynamics. The increasing adoption of cloud services and the Internet of Things (IoT) further widens the scope of user activities that need monitoring. The market is witnessing collaborations between UAM solution providers and other cybersecurity firms to offer comprehensive, integrated solutions. Additionally, the shift towards proactive threat hunting rather than reactive incident response is reshaping the landscape.
Regional Analysis
Geographically, the adoption of User Activity Monitoring (UAM) solutions is widespread, with North America leading the market due to its strong cybersecurity posture and stringent regulatory environment. Europe follows suit, driven by the General Data Protection Regulation (GDPR) compliance requirements. The Asia Pacific region presents a burgeoning market opportunity, propelled by the rapid digitization of businesses and a growing awareness of cybersecurity.
Competitive Landscape
Leading Companies in User Activity Monitoring (UAM) Solutions Market:
Please note: This is a preliminary list; the final study will feature 18–20 leading companies in this market. The selection of companies in the final report can be customized based on our client’s specific requirements.
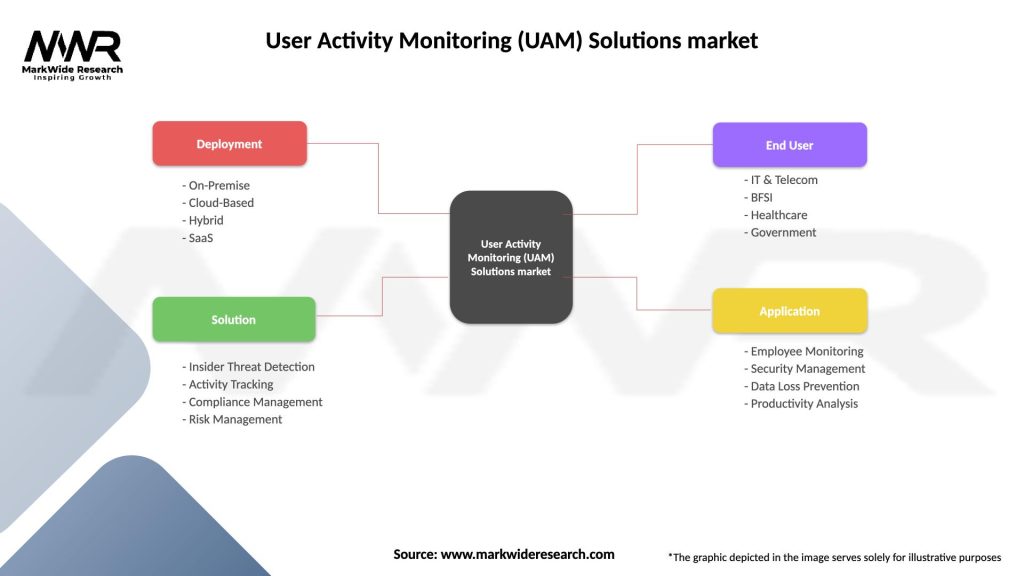
Segmentation
The UAM solutions market can be segmented based on deployment type, organization size, industry vertical, and geography. Deployment types include on-premises, cloud-based, and hybrid solutions. Organization sizes range from small and medium-sized enterprises (SMEs) to large enterprises. Industry verticals span healthcare, finance, IT and telecommunications, government, and more.
Category-wise Insights
UAM solutions can be categorized into user behavior analytics, log analysis, auditing and reporting, and real-time monitoring. User behavior analytics leverage machine learning to identify deviations from normal user activities. Log analysis involves analyzing logs to detect patterns and anomalies. Auditing and reporting offer compliance-centric features, while real-time monitoring ensures immediate threat detection.
Key Benefits for Industry Participants and Stakeholders
Investing in User Activity Monitoring (UAM) solutions yields numerous benefits. Organizations gain real-time visibility into user activities, enabling swift response to potential threats. Compliance requirements are met through detailed activity tracking and audit trails. Insider threats are mitigated, safeguarding sensitive data. Ultimately, businesses fortify their cybersecurity stance, enhancing trust among customers and partners.
SWOT Analysis
Market Key Trends
Key trends shaping the UAM solutions market include the integration of User and Entity Behavior Analytics (UEBA), the emergence of cloud-native UAM solutions, and the focus on automated incident response. Additionally, the convergence of UAM with Identity and Access Management (IAM) solutions is gaining traction, enabling comprehensive user-centric security approaches.
Covid-19 Impact
The COVID-19 pandemic has catalyzed the adoption of UAM solutions. With remote work becoming the norm, organizations faced heightened cybersecurity risks. UAM solutions played a crucial role in monitoring remote employee activities, ensuring data security, and mitigating insider threats during the pandemic-induced digital transformation.
Key Industry Developments
Recent developments include partnerships between UAM solution providers and Managed Security Service Providers (MSSPs) to deliver enhanced threat detection and response capabilities. Furthermore, integration with Security Orchestration, Automation, and Response (SOAR) platforms is streamlining incident management workflows.
Analyst Suggestions
Industry analysts recommend that organizations prioritize UAM solutions as part of their cybersecurity strategies. Implementing a holistic approach that combines UAM with other cybersecurity measures like endpoint protection, network monitoring, and employee training can effectively mitigate a wide range of security risks.
Future Outlook
The future of the User Activity Monitoring (UAM) solutions market is promising. As cyber threats continue to evolve, UAM solutions will play an increasingly crucial role in identifying and mitigating risks. Integration with emerging technologies like Zero Trust Architecture and Continuous Authentication will reshape UAM capabilities, offering even more sophisticated protection.
Conclusion
In the rapidly changing digital landscape, User Activity Monitoring (UAM) solutions stand as a bulwark against insider threats and cyberattacks. By providing insights into user behavior and activities, UAM solutions empower organizations to take proactive measures to safeguard their digital assets. As the market evolves, embracing UAM alongside innovative technologies will be pivotal in ensuring the resilience and security of businesses across sectors.
What is User Activity Monitoring (UAM) Solutions?
User Activity Monitoring (UAM) Solutions refer to tools and technologies that track and analyze user behavior within digital environments. These solutions are commonly used to enhance security, improve compliance, and optimize user experience across various applications and platforms.
What are the key players in the User Activity Monitoring (UAM) Solutions market?
Key players in the User Activity Monitoring (UAM) Solutions market include companies like Teramind, ActivTrak, and Veriato, which provide comprehensive monitoring and analytics tools. These companies focus on enhancing organizational security and productivity through user behavior insights, among others.
What are the main drivers of growth in the User Activity Monitoring (UAM) Solutions market?
The growth of the User Activity Monitoring (UAM) Solutions market is driven by increasing concerns over data security, the rise of remote work, and the need for compliance with regulations. Organizations are adopting UAM solutions to mitigate risks associated with insider threats and to ensure adherence to data protection laws.
What challenges does the User Activity Monitoring (UAM) Solutions market face?
The User Activity Monitoring (UAM) Solutions market faces challenges such as privacy concerns and potential resistance from employees regarding surveillance. Additionally, integrating UAM solutions with existing IT infrastructure can be complex and resource-intensive.
What opportunities exist in the User Activity Monitoring (UAM) Solutions market?
Opportunities in the User Activity Monitoring (UAM) Solutions market include the development of advanced analytics and AI-driven insights to enhance user behavior understanding. As organizations increasingly prioritize cybersecurity, the demand for innovative UAM solutions is expected to grow.
What trends are shaping the User Activity Monitoring (UAM) Solutions market?
Trends in the User Activity Monitoring (UAM) Solutions market include the integration of machine learning for predictive analytics and the shift towards cloud-based monitoring solutions. Additionally, there is a growing emphasis on user privacy and ethical monitoring practices.
User Activity Monitoring (UAM) Solutions market
| Segmentation Details | Description |
|---|---|
| Deployment | On-Premise, Cloud-Based, Hybrid, SaaS |
| Solution | Insider Threat Detection, Activity Tracking, Compliance Management, Risk Management |
| End User | IT & Telecom, BFSI, Healthcare, Government |
| Application | Employee Monitoring, Security Management, Data Loss Prevention, Productivity Analysis |
Please note: The segmentation can be entirely customized to align with our client’s needs.
Leading Companies in User Activity Monitoring (UAM) Solutions Market:
Please note: This is a preliminary list; the final study will feature 18–20 leading companies in this market. The selection of companies in the final report can be customized based on our client’s specific requirements.
North America
o US
o Canada
o Mexico
Europe
o Germany
o Italy
o France
o UK
o Spain
o Denmark
o Sweden
o Austria
o Belgium
o Finland
o Turkey
o Poland
o Russia
o Greece
o Switzerland
o Netherlands
o Norway
o Portugal
o Rest of Europe
Asia Pacific
o China
o Japan
o India
o South Korea
o Indonesia
o Malaysia
o Kazakhstan
o Taiwan
o Vietnam
o Thailand
o Philippines
o Singapore
o Australia
o New Zealand
o Rest of Asia Pacific
South America
o Brazil
o Argentina
o Colombia
o Chile
o Peru
o Rest of South America
The Middle East & Africa
o Saudi Arabia
o UAE
o Qatar
o South Africa
o Israel
o Kuwait
o Oman
o North Africa
o West Africa
o Rest of MEA
Trusted by Global Leaders
Fortune 500 companies, SMEs, and top institutions rely on MWR’s insights to make informed decisions and drive growth.
ISO & IAF Certified
Our certifications reflect a commitment to accuracy, reliability, and high-quality market intelligence trusted worldwide.
Customized Insights
Every report is tailored to your business, offering actionable recommendations to boost growth and competitiveness.
Multi-Language Support
Final reports are delivered in English and major global languages including French, German, Spanish, Italian, Portuguese, Chinese, Japanese, Korean, Arabic, Russian, and more.
Unlimited User Access
Corporate License offers unrestricted access for your entire organization at no extra cost.
Free Company Inclusion
We add 3–4 extra companies of your choice for more relevant competitive analysis — free of charge.
Post-Sale Assistance
Dedicated account managers provide unlimited support, handling queries and customization even after delivery.
GET A FREE SAMPLE REPORT
This free sample study provides a complete overview of the report, including executive summary, market segments, competitive analysis, country level analysis and more.
ISO AND IAF CERTIFIED


GET A FREE SAMPLE REPORT
This free sample study provides a complete overview of the report, including executive summary, market segments, competitive analysis, country level analysis and more.
ISO AND IAF CERTIFIED


Suite #BAA205 Torrance, CA 90503 USA
24/7 Customer Support
Email us at