444 Alaska Avenue
Suite #BAA205 Torrance, CA 90503 USA
+1 424 999 9627
24/7 Customer Support
sales@markwideresearch.com
Email us at
Suite #BAA205 Torrance, CA 90503 USA
24/7 Customer Support
Email us at

Corporate User License
Unlimited User Access, Post-Sale Support, Free Updates, Reports in English & Major Languages, and more
$3450
The mobile device user authentication as a service market represents a rapidly evolving segment within the broader cybersecurity landscape, driven by the exponential growth of mobile device usage and increasing security concerns across enterprises and consumer applications. This market encompasses cloud-based authentication solutions that verify user identities through various methods including biometric authentication, multi-factor authentication, and behavioral analytics specifically designed for mobile platforms.
Market dynamics indicate substantial growth momentum, with the sector experiencing a compound annual growth rate (CAGR) of 18.7% as organizations prioritize mobile security infrastructure. The proliferation of remote work arrangements and bring-your-own-device (BYOD) policies has accelerated demand for robust authentication services that can seamlessly integrate with diverse mobile ecosystems while maintaining stringent security standards.
Enterprise adoption has been particularly pronounced, with 73% of organizations implementing some form of mobile authentication service to protect sensitive corporate data and applications. The market benefits from technological advancements in artificial intelligence, machine learning, and biometric recognition technologies, which have significantly enhanced the accuracy and user experience of mobile authentication solutions.
Regional distribution shows North America leading market adoption with approximately 42% market share, followed by Europe and Asia-Pacific regions experiencing rapid growth due to increasing smartphone penetration and digital transformation initiatives across various industry verticals.
The mobile device user authentication as a service market refers to the comprehensive ecosystem of cloud-based security solutions that verify and validate user identities specifically for mobile devices and applications. This market encompasses various authentication methodologies delivered through software-as-a-service (SaaS) models, enabling organizations to implement robust security measures without maintaining extensive on-premises infrastructure.
Authentication services in this context include biometric verification systems utilizing fingerprint scanning, facial recognition, voice authentication, and iris scanning technologies. Additionally, the market covers multi-factor authentication solutions that combine something users know (passwords), something they have (mobile devices), and something they are (biometric characteristics) to create layered security approaches.
Service delivery models typically involve cloud-based platforms that integrate with existing mobile applications and enterprise systems through application programming interfaces (APIs) and software development kits (SDKs). These solutions provide real-time authentication capabilities while offering scalability, flexibility, and cost-effectiveness compared to traditional on-premises authentication infrastructure.
Market expansion in the mobile device user authentication as a service sector reflects the convergence of several critical technology trends and business imperatives. Organizations across industries are increasingly recognizing the necessity of implementing sophisticated authentication mechanisms to protect against evolving cyber threats while accommodating the growing mobile workforce and customer base.
Key growth drivers include the rising incidence of mobile-based cyber attacks, regulatory compliance requirements, and the need for seamless user experiences that balance security with convenience. The market has witnessed significant innovation in passwordless authentication technologies, with 67% of enterprises expressing interest in eliminating traditional password-based systems in favor of more secure and user-friendly alternatives.
Competitive landscape features a diverse mix of established cybersecurity vendors, specialized authentication service providers, and emerging technology companies leveraging artificial intelligence and machine learning capabilities. Strategic partnerships and acquisitions have become common as companies seek to expand their authentication service portfolios and geographic reach.
Future projections indicate continued robust growth driven by increasing mobile device adoption, evolving regulatory frameworks, and advancing biometric technologies that promise enhanced security and improved user experiences across various application scenarios.
Market intelligence reveals several critical insights that define the current state and future trajectory of the mobile device user authentication as a service market:
Security threat evolution represents the primary catalyst driving market expansion, as cybercriminals increasingly target mobile devices and applications with sophisticated attack vectors. The rise in mobile malware, phishing attempts, and identity theft incidents has compelled organizations to implement more robust authentication mechanisms beyond traditional username and password combinations.
Regulatory compliance requirements across various industries mandate stronger authentication protocols, particularly in financial services, healthcare, and government sectors. Regulations such as PCI DSS, HIPAA, and GDPR require organizations to implement multi-factor authentication and maintain detailed audit trails of user access activities, driving demand for comprehensive authentication services.
Remote work proliferation has fundamentally altered enterprise security requirements, with organizations needing to authenticate users accessing corporate resources from diverse locations and devices. The shift toward distributed workforces has increased the importance of reliable, scalable authentication solutions that can verify user identities regardless of geographic location or network conditions.
Digital transformation initiatives across industries have accelerated mobile application development and deployment, creating new authentication requirements for customer-facing applications, employee productivity tools, and partner collaboration platforms. Organizations seek authentication services that can seamlessly integrate with their digital transformation strategies while maintaining security standards.
User experience expectations continue to evolve, with consumers and employees demanding frictionless authentication processes that don’t compromise security. The market responds with innovative solutions that balance robust security measures with intuitive user interfaces and rapid authentication processing times.
Implementation complexity poses significant challenges for organizations considering mobile authentication services, particularly those with legacy systems and complex IT infrastructures. Integration difficulties, compatibility issues, and the need for extensive testing can delay deployment timelines and increase implementation costs, potentially deterring adoption among smaller organizations.
Privacy concerns surrounding biometric data collection and storage create hesitation among users and organizations regarding authentication service adoption. Concerns about biometric data breaches, unauthorized access to personal information, and compliance with privacy regulations can slow market growth, particularly in privacy-conscious regions and industries.
Technology limitations in certain authentication methods can impact reliability and user acceptance. False positive and false negative rates in biometric authentication, device compatibility issues, and performance variations across different mobile platforms can create user frustration and reduce overall system effectiveness.
Cost considerations remain a significant barrier for smaller organizations and startups that may find comprehensive authentication services financially challenging. Subscription-based pricing models, integration costs, and ongoing maintenance expenses can strain budgets, particularly for organizations with limited IT resources and cybersecurity expertise.
Standardization gaps across the industry create interoperability challenges and vendor lock-in concerns. The lack of universal standards for authentication protocols and data formats can complicate multi-vendor environments and limit organizational flexibility in choosing and switching between service providers.
Emerging market expansion presents substantial growth opportunities as developing regions experience rapid smartphone adoption and digital infrastructure development. Countries in Asia-Pacific, Latin America, and Africa offer significant potential for authentication service providers willing to adapt their solutions to local market conditions and regulatory requirements.
Industry vertical specialization creates opportunities for authentication service providers to develop tailored solutions for specific sectors such as healthcare, education, retail, and manufacturing. Specialized authentication services that address unique industry requirements and compliance standards can command premium pricing and establish strong market positions.
Artificial intelligence integration offers opportunities to enhance authentication accuracy and user experience through advanced behavioral analytics, risk assessment algorithms, and adaptive authentication protocols. AI-powered solutions can provide more sophisticated threat detection capabilities and personalized authentication experiences based on user behavior patterns.
Internet of Things (IoT) convergence creates new authentication requirements as mobile devices increasingly interact with connected devices and smart systems. Authentication services that can seamlessly extend to IoT ecosystems and provide unified identity management across diverse device types represent significant market opportunities.
Partnership opportunities with mobile device manufacturers, application developers, and enterprise software vendors can accelerate market penetration and create integrated authentication ecosystems. Strategic alliances can provide access to larger customer bases and enable the development of more comprehensive security solutions.
Competitive intensity within the mobile device user authentication as a service market continues to escalate as established cybersecurity companies, technology giants, and specialized startups compete for market share. This competitive environment drives continuous innovation, pricing pressures, and the need for differentiated value propositions that address specific customer requirements and use cases.
Technology convergence is reshaping market dynamics as authentication services increasingly incorporate artificial intelligence, machine learning, and advanced analytics capabilities. According to MarkWide Research analysis, organizations implementing AI-enhanced authentication solutions report 34% improvement in threat detection accuracy compared to traditional methods.
Customer expectations are evolving rapidly, with users demanding authentication solutions that provide enterprise-grade security without compromising convenience or performance. This trend drives service providers to develop more sophisticated user experience designs and implement advanced technologies that can deliver both security and usability.
Regulatory landscape changes continue to influence market dynamics as governments worldwide implement new data protection and cybersecurity requirements. These regulatory developments create both opportunities for compliant service providers and challenges for organizations that must adapt their authentication strategies to meet evolving legal requirements.
Supply chain considerations have become increasingly important as organizations evaluate authentication service providers based on their ability to maintain service availability, data security, and compliance across global operations. Vendor reliability and geographic service coverage significantly influence customer selection criteria and market positioning strategies.
Data collection approaches for analyzing the mobile device user authentication as a service market employ comprehensive methodologies combining primary research, secondary analysis, and industry expert consultations. Research teams utilize structured surveys, in-depth interviews, and focus group discussions with key stakeholders including enterprise decision-makers, technology vendors, and end users.
Primary research activities involve direct engagement with market participants through telephone interviews, online surveys, and face-to-face meetings with executives from authentication service providers, enterprise customers, and technology integrators. These interactions provide valuable insights into market trends, customer preferences, competitive dynamics, and future growth projections.
Secondary research sources include industry reports, company financial statements, regulatory filings, patent databases, and academic publications related to mobile security and authentication technologies. This comprehensive approach ensures thorough coverage of market developments, technological advancements, and competitive landscape evolution.
Data validation processes employ triangulation methods that cross-reference information from multiple sources to ensure accuracy and reliability. Research teams conduct fact-checking procedures, verify statistical data through independent sources, and validate findings through expert review panels comprising industry professionals and academic researchers.
Analytical frameworks utilize both quantitative and qualitative analysis techniques to interpret market data and identify meaningful trends. Statistical modeling, regression analysis, and predictive algorithms help project future market developments while qualitative analysis provides context and explains underlying market dynamics.
North American market leadership stems from early technology adoption, robust cybersecurity awareness, and stringent regulatory requirements across various industries. The region benefits from a mature enterprise technology infrastructure and high smartphone penetration rates, with 89% of businesses implementing some form of mobile authentication solution.
European market growth is driven by GDPR compliance requirements and increasing focus on data privacy protection. The region shows strong adoption in financial services and healthcare sectors, with Nordic countries leading in biometric authentication implementation. European organizations prioritize authentication solutions that demonstrate clear compliance with regional privacy regulations.
Asia-Pacific expansion represents the fastest-growing regional market, fueled by rapid smartphone adoption, digital transformation initiatives, and increasing cybersecurity awareness. Countries such as China, India, and Japan show particularly strong growth in mobile authentication services, with 26% annual growth rate in enterprise adoption across the region.
Latin American emergence reflects growing digital infrastructure development and increasing mobile banking adoption. Brazil and Mexico lead regional growth, with authentication service providers adapting solutions to address local market conditions, language requirements, and regulatory frameworks.
Middle East and Africa development shows promising growth potential driven by government digitization initiatives and increasing mobile device penetration. The region presents opportunities for authentication service providers willing to address unique market challenges including infrastructure limitations and diverse regulatory environments.
Market leadership in the mobile device user authentication as a service sector is characterized by a diverse ecosystem of established technology companies, specialized security vendors, and innovative startups. The competitive environment features both horizontal players offering comprehensive authentication platforms and vertical specialists focusing on specific authentication methods or industry segments.
Key market participants include:
Competitive strategies focus on differentiation through advanced technology integration, industry-specific solutions, and comprehensive customer support services. Companies invest heavily in research and development to enhance authentication accuracy, reduce processing latency, and improve user experience across diverse mobile platforms and use cases.
By Authentication Method:
By Deployment Model:
By End-User Industry:
Biometric Authentication Segment dominates the market due to superior security characteristics and improving user acceptance rates. Fingerprint authentication leads this category with widespread mobile device integration, while facial recognition shows rapid growth driven by advancing computer vision technologies and improved accuracy rates.
Multi-Factor Authentication Solutions experience strong enterprise adoption as organizations seek layered security approaches that combine multiple verification methods. This segment benefits from regulatory requirements mandating stronger authentication protocols and growing awareness of single-factor authentication vulnerabilities.
Cloud-Based Deployment Models represent the fastest-growing segment as organizations prioritize scalability, cost-effectiveness, and rapid deployment capabilities. Cloud services offer advantages including automatic updates, global availability, and reduced infrastructure management requirements that appeal to diverse organizational sizes and industries.
Financial Services Applications drive significant market demand due to stringent regulatory requirements and high-value transaction protection needs. This sector shows particular interest in advanced authentication methods that can prevent fraud while maintaining positive customer experiences during digital banking interactions.
Healthcare Industry Adoption accelerates driven by patient data protection requirements and increasing digitization of medical records and treatment systems. Healthcare organizations seek authentication solutions that comply with HIPAA regulations while supporting diverse user types including medical professionals, patients, and administrative staff.
Enhanced Security Posture represents the primary benefit for organizations implementing mobile device user authentication services. These solutions provide multiple layers of protection against unauthorized access, identity theft, and data breaches while maintaining detailed audit trails for compliance and forensic analysis purposes.
Improved User Experience through streamlined authentication processes that eliminate complex password requirements and reduce login friction. Modern authentication services offer seamless single sign-on capabilities and adaptive authentication that adjusts security requirements based on risk assessment and user behavior patterns.
Cost Optimization through cloud-based service models that eliminate the need for extensive on-premises authentication infrastructure. Organizations benefit from predictable subscription pricing, reduced IT maintenance overhead, and scalable capacity that adjusts to changing business requirements without significant capital investments.
Regulatory Compliance support through authentication solutions designed to meet industry-specific requirements and data protection regulations. Service providers offer compliance documentation, audit support, and regulatory update management that helps organizations maintain adherence to evolving legal requirements.
Operational Efficiency gains through automated authentication processes, centralized identity management, and reduced help desk support requirements. Organizations report significant reductions in password-related support tickets and improved productivity through faster, more reliable authentication experiences.
Scalability and Flexibility advantages that allow organizations to adapt authentication requirements as business needs evolve. Cloud-based services provide elastic capacity, global availability, and rapid deployment capabilities that support business growth and geographic expansion initiatives.
Strengths:
Weaknesses:
Opportunities:
Threats:
Passwordless Authentication Adoption represents a fundamental shift in market direction as organizations seek to eliminate password-related security vulnerabilities and user friction. This trend drives development of advanced biometric solutions, hardware security keys, and behavioral authentication methods that provide superior security without traditional password requirements.
Zero Trust Architecture Integration influences authentication service development as organizations adopt comprehensive security frameworks that verify every access request regardless of user location or device. Authentication services increasingly incorporate continuous verification capabilities and risk-based access controls that align with zero trust principles.
Artificial Intelligence Enhancement transforms authentication capabilities through machine learning algorithms that improve accuracy, detect anomalous behavior, and provide adaptive security responses. MWR data indicates that AI-powered authentication solutions demonstrate 45% better threat detection rates compared to traditional rule-based systems.
Mobile-First Design Philosophy drives authentication service development with emphasis on mobile user interfaces, touch-optimized experiences, and mobile-specific security features. Service providers prioritize mobile platform optimization to address the growing prevalence of mobile device usage in enterprise and consumer applications.
Privacy-Preserving Technologies gain importance as organizations seek authentication solutions that protect user privacy while maintaining security effectiveness. Technologies such as homomorphic encryption, differential privacy, and federated learning enable secure authentication without exposing sensitive biometric or behavioral data.
Industry-Specific Customization becomes increasingly important as different sectors require tailored authentication approaches that address unique regulatory requirements, user types, and security threats. Healthcare, financial services, and government sectors drive demand for specialized authentication solutions with industry-specific features and compliance capabilities.
Strategic Acquisitions continue to reshape the competitive landscape as established technology companies acquire specialized authentication service providers to expand their security portfolios. Recent acquisitions demonstrate the strategic importance of mobile authentication capabilities in comprehensive cybersecurity offerings.
Partnership Expansions between authentication service providers and mobile device manufacturers create integrated security ecosystems that leverage hardware-based security features. These partnerships enable more sophisticated authentication methods and improved user experiences through deeper platform integration.
Regulatory Compliance Enhancements drive service providers to develop authentication solutions that address evolving data protection and cybersecurity regulations. New compliance features, audit capabilities, and privacy controls help organizations meet regulatory requirements while maintaining operational efficiency.
Technology Integration Advances enable authentication services to incorporate emerging technologies such as 5G connectivity, edge computing, and advanced biometric sensors. These integrations improve authentication speed, accuracy, and reliability while supporting new use cases and deployment scenarios.
Open Standards Adoption promotes interoperability and reduces vendor lock-in concerns through industry-wide collaboration on authentication protocols and data formats. Standards development efforts focus on creating unified approaches that support multi-vendor environments and customer flexibility.
Investment Activity in authentication technology startups demonstrates continued market confidence and innovation potential. Venture capital funding supports development of next-generation authentication methods and specialized solutions for emerging market segments and use cases.
Technology Investment Priorities should focus on artificial intelligence and machine learning capabilities that enhance authentication accuracy and provide adaptive security features. Organizations should evaluate authentication service providers based on their AI integration roadmaps and demonstrated improvements in threat detection and user experience.
Implementation Strategy Recommendations emphasize phased deployment approaches that begin with pilot programs in specific user groups or applications before expanding to enterprise-wide implementations. This approach allows organizations to validate authentication service effectiveness and address integration challenges before full-scale deployment.
Vendor Selection Criteria should prioritize service providers with strong compliance capabilities, extensive integration options, and proven scalability track records. Organizations should evaluate authentication services based on their ability to support current requirements while adapting to future business needs and regulatory changes.
Security Framework Integration requires authentication services that align with broader cybersecurity strategies including zero trust architectures, identity governance programs, and incident response procedures. Organizations should select solutions that complement existing security investments and support comprehensive protection strategies.
User Experience Optimization demands careful balance between security requirements and usability considerations. Organizations should prioritize authentication solutions that provide strong security while minimizing user friction and supporting diverse device types and usage scenarios.
Compliance Planning should anticipate evolving regulatory requirements and select authentication services with demonstrated ability to adapt to changing compliance landscapes. Organizations should evaluate service providers based on their regulatory expertise and track record of supporting customer compliance initiatives.
Market expansion projections indicate continued robust growth driven by increasing mobile device adoption, evolving security threats, and expanding regulatory requirements across global markets. The sector is expected to maintain strong momentum with projected CAGR of 19.2% through the next five-year period as organizations prioritize mobile security investments.
Technology evolution will likely focus on advanced biometric methods, quantum-resistant cryptography, and enhanced artificial intelligence capabilities that provide more sophisticated threat detection and user behavior analysis. These technological advances promise to improve authentication accuracy while reducing false positive rates and user friction.
Geographic expansion opportunities will emerge in developing markets as smartphone penetration increases and digital infrastructure develops. Asia-Pacific and Latin American regions show particular promise for authentication service providers willing to adapt solutions to local market conditions and regulatory requirements.
Industry convergence trends suggest increasing integration between authentication services and broader cybersecurity platforms, identity governance solutions, and enterprise mobility management systems. This convergence will create more comprehensive security ecosystems that address multiple aspects of mobile device and user security.
Regulatory developments will continue to influence market direction as governments worldwide implement new data protection and cybersecurity requirements. Authentication service providers must maintain flexibility to adapt to evolving compliance landscapes while supporting customer regulatory obligations.
Innovation acceleration in areas such as behavioral biometrics, continuous authentication, and privacy-preserving technologies will create new market opportunities and competitive differentiators. According to MarkWide Research projections, organizations implementing advanced authentication technologies report 58% reduction in security incidents compared to traditional authentication methods.
The mobile device user authentication as a service market represents a dynamic and rapidly expanding sector within the broader cybersecurity landscape, driven by fundamental shifts in how organizations and individuals interact with mobile technology. The convergence of increasing security threats, regulatory compliance requirements, and evolving user expectations creates a compelling market environment for innovative authentication solutions that balance robust security with exceptional user experiences.
Market fundamentals remain strong across all key indicators, with sustained growth momentum supported by technological advancement, expanding mobile device adoption, and increasing cybersecurity awareness across diverse industry verticals. The shift toward cloud-based service models and the integration of artificial intelligence capabilities position the market for continued expansion and innovation.
Strategic opportunities abound for organizations that can effectively navigate the complex landscape of technology integration, regulatory compliance, and user experience optimization. Success in this market requires deep understanding of customer requirements, technological capabilities, and evolving security threats that shape authentication service development and deployment strategies.
The future trajectory of the mobile device user authentication as a service market points toward continued growth, technological sophistication, and expanding global adoption as organizations recognize the critical importance of mobile security in their overall cybersecurity strategies and digital transformation initiatives.
What is Mobile Device User Authentication As a Service?
Mobile Device User Authentication As a Service refers to cloud-based solutions that provide secure authentication methods for users accessing mobile devices. This service typically includes biometric authentication, multi-factor authentication, and single sign-on capabilities to enhance security and user experience.
What are the key companies in the Mobile Device User Authentication As a Service Market?
Key companies in the Mobile Device User Authentication As a Service Market include Okta, Auth0, and Microsoft, which offer various authentication solutions tailored for mobile applications and devices, among others.
What are the growth factors driving the Mobile Device User Authentication As a Service Market?
The growth of the Mobile Device User Authentication As a Service Market is driven by the increasing need for enhanced security in mobile applications, the rise in mobile device usage, and the growing adoption of remote work practices that require secure access to corporate resources.
What challenges does the Mobile Device User Authentication As a Service Market face?
Challenges in the Mobile Device User Authentication As a Service Market include concerns over data privacy, the complexity of integrating authentication solutions with existing systems, and the potential for user resistance to adopting new authentication methods.
What opportunities exist in the Mobile Device User Authentication As a Service Market?
Opportunities in the Mobile Device User Authentication As a Service Market include the development of advanced biometric technologies, the integration of artificial intelligence for fraud detection, and the expansion of services to cater to emerging markets and industries.
What trends are shaping the Mobile Device User Authentication As a Service Market?
Trends in the Mobile Device User Authentication As a Service Market include the increasing use of biometric authentication methods, the shift towards passwordless authentication solutions, and the growing emphasis on user experience and convenience in security measures.
Mobile Device User Authentication As a Service Market
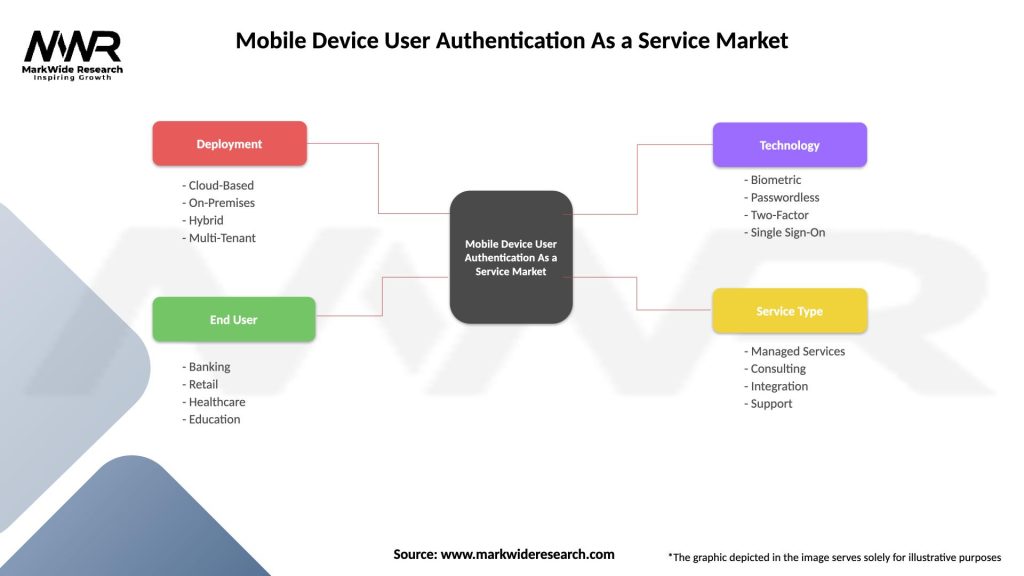
| Segmentation Details | Description |
|---|---|
| Deployment | Cloud-Based, On-Premises, Hybrid, Multi-Tenant |
| End User | Banking, Retail, Healthcare, Education |
| Technology | Biometric, Passwordless, Two-Factor, Single Sign-On |
| Service Type | Managed Services, Consulting, Integration, Support |
Please note: The segmentation can be entirely customized to align with our client’s needs.
Leading companies in the Mobile Device User Authentication As a Service Market
Please note: This is a preliminary list; the final study will feature 18–20 leading companies in this market. The selection of companies in the final report can be customized based on our client’s specific requirements.
North America
o US
o Canada
o Mexico
Europe
o Germany
o Italy
o France
o UK
o Spain
o Denmark
o Sweden
o Austria
o Belgium
o Finland
o Turkey
o Poland
o Russia
o Greece
o Switzerland
o Netherlands
o Norway
o Portugal
o Rest of Europe
Asia Pacific
o China
o Japan
o India
o South Korea
o Indonesia
o Malaysia
o Kazakhstan
o Taiwan
o Vietnam
o Thailand
o Philippines
o Singapore
o Australia
o New Zealand
o Rest of Asia Pacific
South America
o Brazil
o Argentina
o Colombia
o Chile
o Peru
o Rest of South America
The Middle East & Africa
o Saudi Arabia
o UAE
o Qatar
o South Africa
o Israel
o Kuwait
o Oman
o North Africa
o West Africa
o Rest of MEA
Trusted by Global Leaders
Fortune 500 companies, SMEs, and top institutions rely on MWR’s insights to make informed decisions and drive growth.
ISO & IAF Certified
Our certifications reflect a commitment to accuracy, reliability, and high-quality market intelligence trusted worldwide.
Customized Insights
Every report is tailored to your business, offering actionable recommendations to boost growth and competitiveness.
Multi-Language Support
Final reports are delivered in English and major global languages including French, German, Spanish, Italian, Portuguese, Chinese, Japanese, Korean, Arabic, Russian, and more.
Unlimited User Access
Corporate License offers unrestricted access for your entire organization at no extra cost.
Free Company Inclusion
We add 3–4 extra companies of your choice for more relevant competitive analysis — free of charge.
Post-Sale Assistance
Dedicated account managers provide unlimited support, handling queries and customization even after delivery.
GET A FREE SAMPLE REPORT
This free sample study provides a complete overview of the report, including executive summary, market segments, competitive analysis, country level analysis and more.
ISO AND IAF CERTIFIED


GET A FREE SAMPLE REPORT
This free sample study provides a complete overview of the report, including executive summary, market segments, competitive analysis, country level analysis and more.
ISO AND IAF CERTIFIED


Suite #BAA205 Torrance, CA 90503 USA
24/7 Customer Support
Email us at