444 Alaska Avenue
Suite #BAA205 Torrance, CA 90503 USA
+1 424 999 9627
24/7 Customer Support
sales@markwideresearch.com
Email us at
Suite #BAA205 Torrance, CA 90503 USA
24/7 Customer Support
Email us at

Corporate User License
Unlimited User Access, Post-Sale Support, Free Updates, Reports in English & Major Languages, and more
$2150
The India network security and cyber risk management market represents one of the most rapidly evolving technology sectors in the country, driven by increasing digitalization, rising cyber threats, and stringent regulatory compliance requirements. Digital transformation initiatives across industries have created unprecedented demand for comprehensive cybersecurity solutions, positioning India as a critical battleground for network security vendors and service providers.
Market dynamics indicate robust growth potential, with the sector experiencing a compound annual growth rate (CAGR) of 12.8% as organizations prioritize cybersecurity investments. The increasing sophistication of cyber attacks, coupled with the rapid adoption of cloud computing, Internet of Things (IoT), and artificial intelligence technologies, has created a complex threat landscape requiring advanced security solutions.
Government initiatives such as Digital India, Make in India, and the National Cyber Security Strategy have significantly influenced market development. These programs have accelerated digital adoption while simultaneously highlighting the critical importance of robust cybersecurity frameworks. Regulatory compliance requirements, including data protection laws and industry-specific security mandates, continue to drive substantial investments in network security infrastructure.
The market encompasses diverse segments including network security appliances, security software solutions, managed security services, and cyber risk assessment platforms. Enterprise adoption spans across banking and financial services, healthcare, government, manufacturing, and telecommunications sectors, each presenting unique security challenges and requirements.
The India network security and cyber risk management market refers to the comprehensive ecosystem of technologies, services, and solutions designed to protect digital infrastructure, data assets, and network communications from cyber threats while enabling effective risk assessment and mitigation strategies across Indian organizations.
Network security encompasses protective measures implemented to secure computer networks and their accessible resources from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure. This includes firewalls, intrusion detection systems, virtual private networks, and advanced threat protection solutions specifically tailored for the Indian market context.
Cyber risk management involves the systematic identification, assessment, and mitigation of cybersecurity risks that could impact business operations, data integrity, and organizational reputation. This discipline combines technical security measures with strategic risk assessment methodologies to create comprehensive protection frameworks.
The market definition extends beyond traditional security products to include managed security services, security consulting, compliance management, incident response capabilities, and emerging technologies such as artificial intelligence-driven threat detection and automated response systems.
Market expansion in India’s network security and cyber risk management sector reflects the country’s accelerating digital transformation journey and increasing cyber threat sophistication. The convergence of cloud adoption, remote work proliferation, and regulatory compliance requirements has created a robust foundation for sustained market growth.
Key growth drivers include the rising frequency and complexity of cyber attacks, with ransomware incidents increasing by 68% year-over-year, prompting organizations to invest heavily in preventive and responsive security measures. The banking and financial services sector leads adoption, accounting for approximately 35% of total market demand, followed by government and healthcare sectors.
Technology evolution toward artificial intelligence, machine learning, and behavioral analytics has transformed traditional security approaches. Organizations are increasingly adopting zero-trust security models, with implementation rates growing by 45% annually as enterprises recognize the limitations of perimeter-based security strategies.
Market segmentation reveals strong demand across network security appliances, endpoint protection platforms, security information and event management (SIEM) solutions, and managed security services. The managed services segment demonstrates particularly robust growth as organizations seek specialized expertise to address complex security challenges.
Competitive landscape features a mix of global technology leaders and emerging Indian cybersecurity companies, creating a dynamic ecosystem that fosters innovation while addressing local market requirements and regulatory compliance needs.
Strategic market insights reveal fundamental shifts in how Indian organizations approach cybersecurity investments and risk management strategies. The following key insights shape market development:
Digital transformation acceleration serves as the primary catalyst driving India’s network security and cyber risk management market expansion. Organizations across sectors are embracing digital technologies, creating expanded attack surfaces that require comprehensive security solutions.
Regulatory compliance requirements continue to intensify, with new data protection laws and industry-specific security mandates compelling organizations to invest in robust cybersecurity frameworks. The Personal Data Protection Bill and sector-specific regulations in banking, healthcare, and telecommunications create mandatory security investment drivers.
Cyber threat sophistication has reached unprecedented levels, with advanced persistent threats, ransomware attacks, and nation-state sponsored cyber activities targeting Indian organizations. The evolving threat landscape necessitates continuous security infrastructure upgrades and advanced threat detection capabilities.
Cloud adoption proliferation across enterprises has fundamentally altered security requirements. Organizations migrating to cloud environments require specialized security solutions that address unique cloud-based vulnerabilities and compliance requirements.
Remote work normalization following the global pandemic has permanently changed organizational security perimeters. The shift toward distributed workforces requires comprehensive endpoint security, secure remote access solutions, and enhanced network monitoring capabilities.
IoT device proliferation in industrial and consumer applications has created millions of new potential attack vectors. Manufacturing, healthcare, and smart city initiatives require specialized IoT security solutions to protect connected device ecosystems.
Government cybersecurity initiatives including the National Cyber Security Strategy and various digital governance programs provide policy support and funding mechanisms that encourage cybersecurity investments across public and private sectors.
Budget constraints represent a significant challenge for many Indian organizations, particularly small and medium enterprises that struggle to allocate sufficient resources for comprehensive cybersecurity programs. Economic uncertainties and competing technology investment priorities often limit security spending.
Skills shortage in cybersecurity professionals creates implementation and management challenges for organizations seeking to deploy advanced security solutions. The limited availability of qualified security experts drives up costs and delays project implementations.
Complexity of integration with existing IT infrastructure poses technical challenges for organizations attempting to implement comprehensive security solutions. Legacy system compatibility issues and integration complexities can significantly increase deployment costs and timelines.
Awareness gaps among decision-makers regarding emerging cyber threats and appropriate security measures can lead to inadequate security investments. Many organizations underestimate their risk exposure and fail to implement comprehensive protection strategies.
Vendor fragmentation in the cybersecurity market creates confusion for buyers attempting to select appropriate solutions. The proliferation of point solutions and lack of standardization can complicate procurement decisions and increase total cost of ownership.
Compliance complexity arising from multiple overlapping regulatory requirements can overwhelm organizations and create implementation challenges. Navigating various industry-specific and general data protection regulations requires specialized expertise that many organizations lack.
False positive challenges in security monitoring systems can overwhelm security teams and reduce overall effectiveness. High false positive rates in threat detection systems can lead to alert fatigue and missed genuine security incidents.
Artificial intelligence integration presents substantial opportunities for next-generation security solutions that can automatically detect, analyze, and respond to cyber threats. AI-driven security platforms offer the potential to address skills shortages while improving threat detection accuracy and response times.
Managed security services expansion offers significant growth potential as organizations seek to outsource complex security operations to specialized providers. The managed services model addresses skills shortages while providing access to advanced security technologies and expertise.
Industry-specific solutions development creates opportunities for vendors to address unique security requirements in sectors such as healthcare, manufacturing, and financial services. Vertical-focused security solutions can command premium pricing while delivering superior value.
Small and medium enterprise market penetration represents an underserved segment with substantial growth potential. Simplified, cost-effective security solutions designed for SMEs can capture significant market share as these organizations recognize cybersecurity importance.
Cloud security specialization offers opportunities for vendors to develop comprehensive cloud-native security platforms that address the unique challenges of hybrid and multi-cloud environments. Cloud security expertise commands premium valuations in the current market.
Government sector expansion through digital governance initiatives creates substantial opportunities for cybersecurity vendors. Smart city projects, e-governance platforms, and digital service delivery programs require comprehensive security frameworks.
Cybersecurity education and training services present opportunities to address the skills shortage while generating recurring revenue streams. Organizations require ongoing security awareness training and professional development programs for their security teams.
Competitive intensity in India’s network security market has increased significantly as global vendors compete with emerging local players for market share. This competition drives innovation while creating pricing pressures that benefit end customers.
Technology convergence is reshaping market dynamics as traditional security categories merge into comprehensive platforms. The integration of network security, endpoint protection, and cloud security into unified platforms creates new competitive advantages for vendors offering holistic solutions.
Customer expectations have evolved toward demanding integrated security platforms that provide comprehensive visibility and control across hybrid IT environments. Organizations increasingly prefer vendors that can deliver end-to-end security solutions rather than point products.
Regulatory influence continues to shape market dynamics as compliance requirements drive specific technology adoption patterns. Vendors that can demonstrate regulatory compliance capabilities gain significant competitive advantages in regulated industries.
Partnership ecosystems have become critical for market success as no single vendor can address all cybersecurity requirements. Strategic partnerships between technology vendors, system integrators, and managed service providers create comprehensive solution offerings.
Innovation cycles have accelerated as emerging technologies such as artificial intelligence, machine learning, and behavioral analytics become standard features in security solutions. Vendors must continuously innovate to maintain competitive positioning.
According to MarkWide Research analysis, market dynamics indicate a shift toward platform-based security solutions that integrate multiple security functions into unified management interfaces, reflecting customer preferences for simplified security operations.
Primary research methodology encompasses comprehensive interviews with cybersecurity executives, IT decision-makers, and security professionals across various industries in India. This qualitative research provides insights into market trends, technology adoption patterns, and future investment priorities.
Secondary research involves extensive analysis of industry reports, vendor financial statements, government policy documents, and regulatory compliance requirements. This research foundation provides quantitative market data and validates primary research findings.
Market sizing methodology combines top-down and bottom-up approaches to ensure accuracy and reliability. Top-down analysis examines overall IT spending patterns and cybersecurity budget allocations, while bottom-up analysis aggregates vendor revenues and customer deployment data.
Competitive analysis methodology includes detailed evaluation of vendor capabilities, market positioning, and strategic initiatives. This analysis encompasses both established global vendors and emerging Indian cybersecurity companies to provide comprehensive market coverage.
Technology assessment methodology evaluates emerging cybersecurity technologies and their potential market impact. This includes analysis of artificial intelligence, machine learning, blockchain, and quantum computing applications in cybersecurity.
Regulatory analysis methodology examines current and proposed cybersecurity regulations, data protection laws, and industry-specific compliance requirements that influence market development and technology adoption patterns.
Forecast methodology combines quantitative modeling with qualitative expert insights to project market growth trajectories. Multiple scenario analyses account for various economic and technology adoption variables that could influence market development.
Mumbai metropolitan region leads India’s network security market, accounting for approximately 28% of total market demand, driven by the concentration of financial services institutions, multinational corporations, and technology companies. The region’s advanced IT infrastructure and regulatory compliance requirements create substantial cybersecurity investment opportunities.
Delhi National Capital Region represents the second-largest market segment, capturing 24% market share through government sector demand, corporate headquarters, and emerging technology companies. Government cybersecurity initiatives and smart city projects drive significant security infrastructure investments.
Bangalore technology hub demonstrates strong growth in cybersecurity adoption, with 22% market share reflecting the concentration of IT services companies, global capability centers, and technology startups. The region’s technology expertise creates demand for advanced security solutions and managed services.
Chennai industrial corridor shows increasing cybersecurity investments, particularly in manufacturing and automotive sectors, representing 12% of market demand. Industrial IoT security and operational technology protection drive specialized security solution requirements.
Pune technology cluster captures 8% market share through automotive, manufacturing, and IT services sector demand. The region’s growing technology ecosystem creates opportunities for both traditional network security and emerging IoT security solutions.
Hyderabad emerging market demonstrates rapid growth potential with 6% current market share but showing 18% annual growth rate driven by government technology initiatives, pharmaceutical companies, and expanding IT services sector presence.
Tier-2 and Tier-3 cities collectively represent emerging opportunities as digital transformation initiatives reach smaller urban centers. Government e-governance projects and expanding internet connectivity create new cybersecurity requirements in these markets.
Market leadership in India’s network security sector features a diverse ecosystem of global technology giants, specialized cybersecurity vendors, and emerging Indian companies. The competitive landscape reflects the market’s complexity and diverse customer requirements.
Competitive strategies focus on platform consolidation, AI integration, and local market customization. Vendors increasingly emphasize managed services capabilities and partner ecosystem development to address market complexity and customer requirements.
By Technology:
By Deployment Model:
By Organization Size:
By Industry Vertical:
Network Security Appliances continue to dominate market demand, with next-generation firewalls experiencing particularly strong adoption rates. Organizations prioritize integrated threat prevention capabilities that combine traditional firewall functions with advanced threat detection and application control features.
Endpoint Security Solutions have evolved beyond traditional antivirus to encompass advanced threat detection, behavioral analysis, and automated response capabilities. The shift toward remote work has accelerated demand for comprehensive endpoint protection platforms that secure devices regardless of location.
Cloud Security Platforms represent the fastest-growing segment as organizations migrate workloads to cloud environments. Cloud access security brokers and cloud workload protection platforms address unique security challenges in hybrid and multi-cloud architectures.
Identity and Access Management solutions gain prominence as organizations implement zero-trust security models. Multi-factor authentication, privileged access management, and identity governance capabilities become essential components of comprehensive security strategies.
Security Information and Event Management platforms evolve toward security orchestration and automated response capabilities. Organizations seek SIEM solutions that provide actionable intelligence and reduce manual security operations overhead.
Managed Security Services experience robust growth as organizations seek to address cybersecurity skills shortages and operational complexity. Security operations center services, threat hunting, and incident response capabilities become increasingly popular outsourcing options.
Data Loss Prevention solutions gain importance as data protection regulations intensify. Organizations require comprehensive content inspection and data classification capabilities to ensure regulatory compliance and prevent data breaches.
For Technology Vendors:
For End-User Organizations:
For System Integrators and Partners:
For Government and Regulators:
Strengths:
Weaknesses:
Opportunities:
Threats:
Zero Trust Architecture Adoption has emerged as a dominant trend, with organizations abandoning traditional perimeter-based security models in favor of comprehensive identity verification and continuous monitoring approaches. This architectural shift requires fundamental changes in security infrastructure and operational processes.
Artificial Intelligence Integration transforms threat detection and response capabilities, enabling automated analysis of vast security data volumes and rapid threat identification. AI-driven security solutions demonstrate superior accuracy in identifying advanced persistent threats and reducing false positive rates.
Cloud-Native Security Solutions gain prominence as organizations migrate to cloud-first architectures. Traditional security tools prove inadequate for cloud environments, driving demand for purpose-built cloud security platforms that address unique cloud vulnerabilities and compliance requirements.
Security Operations Center Automation becomes essential as organizations struggle with cybersecurity skills shortages and increasing threat volumes. Automated threat hunting, incident response orchestration, and security workflow automation reduce manual operations requirements.
Privacy-Preserving Technologies gain importance as data protection regulations intensify. Homomorphic encryption, differential privacy, and secure multi-party computation enable organizations to maintain security while preserving data privacy and regulatory compliance.
DevSecOps Integration becomes standard practice as organizations embed security throughout software development lifecycles. Security testing automation, vulnerability scanning integration, and secure coding practices become integral components of application development processes.
Extended Detection and Response platforms emerge as comprehensive security solutions that integrate endpoint, network, and cloud security data into unified threat detection and response capabilities, providing holistic security visibility and control.
Regulatory Framework Evolution includes the development of comprehensive data protection legislation and industry-specific cybersecurity mandates. The Personal Data Protection Bill and sector-specific regulations create new compliance requirements driving security investments.
Government Cybersecurity Initiatives encompass the establishment of national cybersecurity agencies, critical infrastructure protection programs, and public-private partnership frameworks supporting cybersecurity development and threat information sharing.
Technology Innovation Acceleration features the emergence of Indian cybersecurity startups developing innovative solutions addressing local market requirements. These companies focus on artificial intelligence, behavioral analytics, and industry-specific security solutions.
Strategic Acquisitions and Partnerships reshape the competitive landscape as global vendors acquire Indian companies to establish local market presence and access specialized expertise. These transactions accelerate technology transfer and market development.
Skills Development Programs include government and industry initiatives to address cybersecurity talent shortages through educational programs, professional certification, and workforce development initiatives supporting industry growth.
Critical Infrastructure Protection initiatives focus on securing power grids, telecommunications networks, financial systems, and transportation infrastructure against cyber threats. These programs create substantial opportunities for specialized security solutions.
International Cooperation Agreements establish frameworks for cybersecurity information sharing, joint threat research, and coordinated incident response capabilities with global partners, enhancing India’s cybersecurity ecosystem.
Investment Prioritization should focus on comprehensive security platforms that integrate multiple security functions rather than point solutions. Organizations benefit from unified security management interfaces and consolidated vendor relationships that reduce complexity and total cost of ownership.
Skills Development requires immediate attention through partnerships with educational institutions, professional certification programs, and managed security service providers. Organizations should develop comprehensive cybersecurity training programs for existing IT staff while leveraging external expertise.
Regulatory Compliance preparation should begin immediately, even for organizations not currently subject to specific regulations. Proactive compliance preparation reduces implementation costs and ensures readiness for evolving regulatory requirements.
Cloud Security Strategy development becomes essential as organizations accelerate cloud adoption. Comprehensive cloud security frameworks should address data protection, identity management, and workload security across hybrid and multi-cloud environments.
Vendor Selection should emphasize partners with strong local presence, comprehensive support capabilities, and proven track records in similar industry verticals. Long-term vendor relationships provide better value than lowest-cost procurement approaches.
Risk Assessment programs should incorporate emerging threats such as supply chain attacks, IoT vulnerabilities, and artificial intelligence-based attacks. Regular risk assessments ensure security investments address actual threat exposures rather than perceived risks.
According to MWR analysis, organizations achieving the best security outcomes combine technology investments with comprehensive governance frameworks, employee training programs, and continuous improvement processes that adapt to evolving threat landscapes.
Market evolution toward integrated security platforms will continue accelerating as organizations seek to reduce vendor complexity and improve security operations efficiency. Platform consolidation creates opportunities for vendors offering comprehensive security suites while challenging point solution providers.
Technology advancement in artificial intelligence and machine learning will fundamentally transform cybersecurity capabilities, enabling predictive threat detection, automated response, and adaptive security policies that evolve with changing threat landscapes. AI integration becomes a competitive necessity rather than optional enhancement.
Regulatory expansion will drive continued market growth as data protection laws mature and industry-specific cybersecurity mandates proliferate. Organizations must prepare for increasingly complex compliance requirements that mandate specific security technologies and operational practices.
Skills shortage challenges will persist, driving continued growth in managed security services and security automation technologies. Organizations increasingly rely on external expertise and automated solutions to address operational complexity and talent limitations.
Cloud security will represent the fastest-growing market segment as organizations complete digital transformation initiatives and migrate critical workloads to cloud environments. Cloud-native security solutions will capture increasing market share from traditional on-premises security tools.
Industry specialization will become more pronounced as vendors develop vertical-specific solutions addressing unique security requirements in healthcare, manufacturing, financial services, and government sectors. Generic security solutions will lose market share to specialized offerings.
International expansion opportunities will emerge as Indian cybersecurity companies leverage domestic expertise to serve global markets. Export potential in cybersecurity services and solutions will contribute to India’s technology sector growth and global competitiveness.
Long-term projections indicate sustained market expansion driven by continuous digital transformation, evolving threat landscapes, and regulatory compliance requirements that create persistent demand for advanced cybersecurity solutions and services.
The India network security and cyber risk management market represents a dynamic and rapidly evolving sector positioned for sustained growth driven by digital transformation acceleration, regulatory compliance requirements, and increasing cyber threat sophistication. Market fundamentals remain strong, supported by government initiatives, expanding technology adoption, and growing cybersecurity awareness across industries.
Strategic opportunities abound for technology vendors, service providers, and end-user organizations willing to invest in comprehensive cybersecurity capabilities. The convergence of artificial intelligence, cloud computing, and zero-trust architectures creates new possibilities for advanced security solutions that address complex threat landscapes while simplifying security operations.
Market challenges including skills shortages, budget constraints, and vendor fragmentation require strategic approaches that emphasize partnership development, managed services adoption, and platform consolidation. Organizations achieving cybersecurity success combine technology investments with comprehensive governance frameworks and continuous improvement processes.
The future outlook for India’s network security and cyber risk management market remains highly positive, with continued expansion expected across all segments and industry verticals. Organizations that proactively invest in cybersecurity capabilities will be best positioned to capitalize on digital transformation opportunities while maintaining robust protection against evolving cyber threats in an increasingly connected business environment.
What is Network Security And Cyber Risk Management?
Network Security And Cyber Risk Management involves the strategies and technologies used to protect networks and data from cyber threats. It encompasses risk assessment, threat detection, and incident response to safeguard sensitive information across various sectors.
What are the key players in the India Network Security And Cyber Risk Management Market?
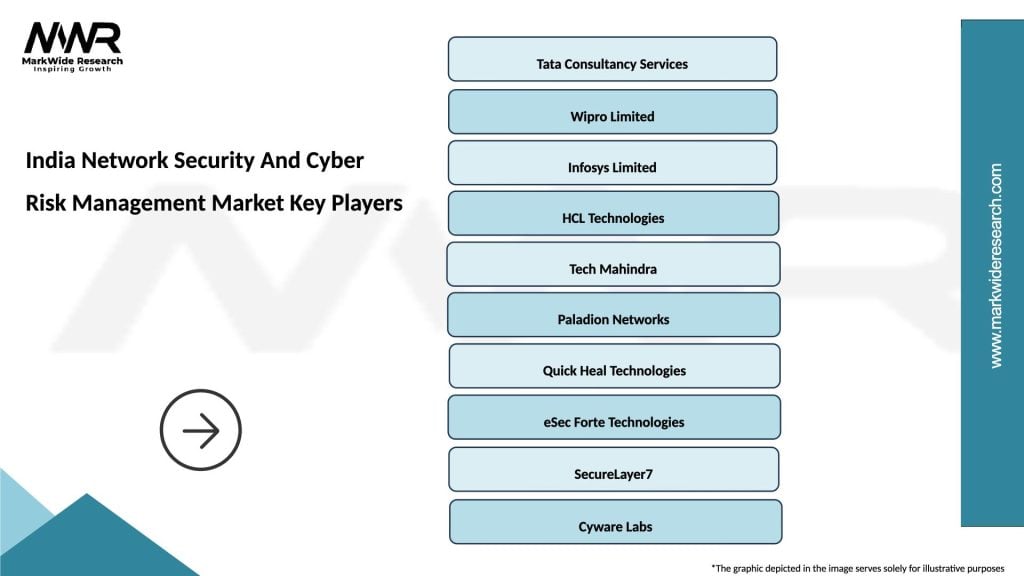
Key players in the India Network Security And Cyber Risk Management Market include companies like Tata Consultancy Services, Wipro, and Infosys, which provide comprehensive cybersecurity solutions and services, among others.
What are the main drivers of growth in the India Network Security And Cyber Risk Management Market?
The growth of the India Network Security And Cyber Risk Management Market is driven by increasing cyber threats, the rise of digital transformation initiatives, and the growing need for compliance with data protection regulations across various industries.
What challenges does the India Network Security And Cyber Risk Management Market face?
Challenges in the India Network Security And Cyber Risk Management Market include the shortage of skilled cybersecurity professionals, the evolving nature of cyber threats, and the complexity of integrating security solutions into existing IT infrastructures.
What opportunities exist in the India Network Security And Cyber Risk Management Market?
Opportunities in the India Network Security And Cyber Risk Management Market include the increasing adoption of cloud security solutions, the demand for advanced threat intelligence services, and the potential for growth in sectors like finance and healthcare that require robust cybersecurity measures.
What trends are shaping the India Network Security And Cyber Risk Management Market?
Trends shaping the India Network Security And Cyber Risk Management Market include the rise of artificial intelligence in threat detection, the growing emphasis on zero-trust security models, and the increasing focus on regulatory compliance and data privacy.
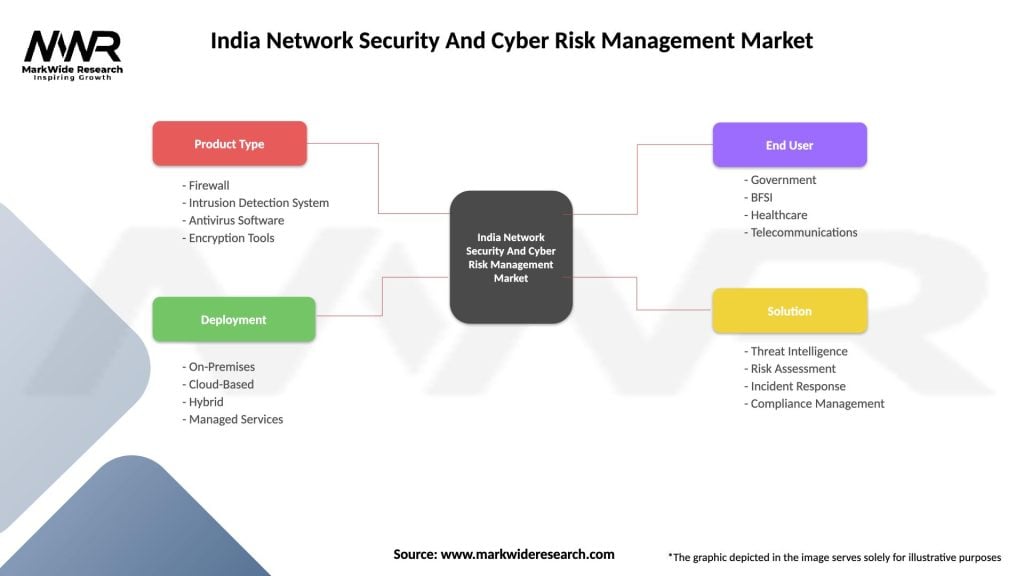
India Network Security And Cyber Risk Management Market
| Segmentation Details | Description |
|---|---|
| Product Type | Firewall, Intrusion Detection System, Antivirus Software, Encryption Tools |
| Deployment | On-Premises, Cloud-Based, Hybrid, Managed Services |
| End User | Government, BFSI, Healthcare, Telecommunications |
| Solution | Threat Intelligence, Risk Assessment, Incident Response, Compliance Management |
Please note: The segmentation can be entirely customized to align with our client’s needs.
Leading companies in the India Network Security And Cyber Risk Management Market
Please note: This is a preliminary list; the final study will feature 18–20 leading companies in this market. The selection of companies in the final report can be customized based on our client’s specific requirements.
Trusted by Global Leaders
Fortune 500 companies, SMEs, and top institutions rely on MWR’s insights to make informed decisions and drive growth.
ISO & IAF Certified
Our certifications reflect a commitment to accuracy, reliability, and high-quality market intelligence trusted worldwide.
Customized Insights
Every report is tailored to your business, offering actionable recommendations to boost growth and competitiveness.
Multi-Language Support
Final reports are delivered in English and major global languages including French, German, Spanish, Italian, Portuguese, Chinese, Japanese, Korean, Arabic, Russian, and more.
Unlimited User Access
Corporate License offers unrestricted access for your entire organization at no extra cost.
Free Company Inclusion
We add 3–4 extra companies of your choice for more relevant competitive analysis — free of charge.
Post-Sale Assistance
Dedicated account managers provide unlimited support, handling queries and customization even after delivery.
GET A FREE SAMPLE REPORT
This free sample study provides a complete overview of the report, including executive summary, market segments, competitive analysis, country level analysis and more.
ISO AND IAF CERTIFIED


GET A FREE SAMPLE REPORT
This free sample study provides a complete overview of the report, including executive summary, market segments, competitive analysis, country level analysis and more.
ISO AND IAF CERTIFIED


Suite #BAA205 Torrance, CA 90503 USA
24/7 Customer Support
Email us at